
What is public key cryptography?
Public key cryptography is one of the most secure ways to send and receive information online. It uses two keys to transmit information safely: a public key and a private key. Think of the public key like a padlock. Anyone can use it to 'lock' the data. The private key, held only by the receiver, is used to 'unlock' the data.
Public key cryptography, also known as asymmetric cryptography, is part of our daily lives on the internet. It keeps emails and messages private and secure, and in the world of cryptocurrencies like Bitcoin, it's what makes sure transactions are safe and that digital money goes to the right person. Let’s take a deeper look at how this essential technology operates.
What are public and private keys?
Before diving into the finer points of cryptography, it's essential to understand what public and private keys are, and how they work.
Public key
A public key is a bit like a bank account number. It's a string of characters that you can share with others.
In the context of blockchain and cryptocurrencies, your public key is used to generate your wallet address, so others can send you funds. However, it does not provide access to the assets in your wallet.
Private key
Think of this as like a banking PIN. It's a secret string of characters that you should never share with anyone.
In blockchain transactions, your private key is used to sign transactions, proving ownership of your digital assets.
The relationship between public and private keys
A public key serves as a digital identifier that can be safely shared with others.
For example, in secure email communication, a sender encrypts the message using the recipient's public key. Only the recipient can decrypt this message with their private key, ensuring the message's confidentiality.
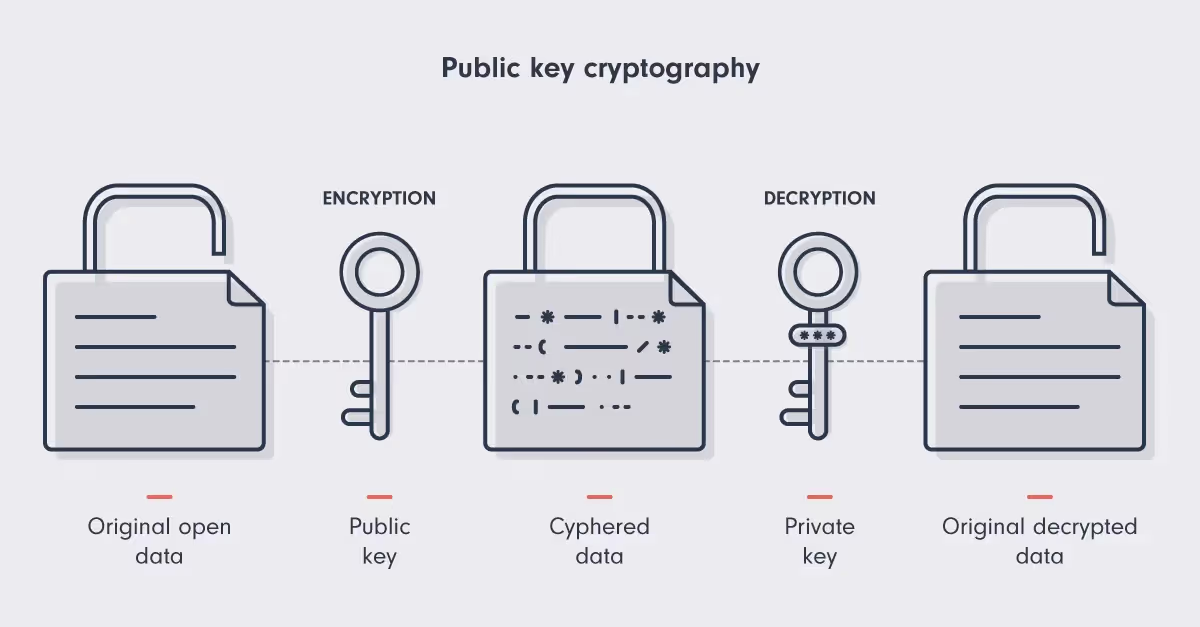
The private key is used to generate the public key. However, this needs to be done in such a way that no one could ever guess the private key based on the public key. This is where cryptography comes in.
Thanks to cryptographic algorithms, while it's straightforward to generate a public key from a private key, reversing this process and deriving the private key from the public key is computationally impossible.
Let’s take a closer look at how the keys are generated, and what makes them so secure.
How are keys generated?
The generation of public and private key pairs is a critical aspect of public key cryptography, involving complex algorithms to ensure security.
Private key generation
The private key is generated first. This involves creating a truly random number. The greater the degree of randomness (also known as entropy), the better. This makes the private key more secure and harder to guess or replicate.
The likelihood of guessing a private key is extremely low. It’s about as likely as finding a specific grain of sand in the vastness of the universe.
However, the Achilles' heel lies in the source of randomness. If attackers can predict or replicate the method used to generate the private key, they could potentially compromise its security.
Random Number Generation (RNG) modules generate private keys. To ensure the number is as random as possible, they can use several sources such as:
- The processes running on a computer's processor
- Physical inputs like mouse movements or keystrokes
- Environmental inputs from camera and microphone data
- A combination of these and other complex sources.
By pulling randomness from these various sources, the RNG module creates a private key that is unique and virtually impossible to replicate or predict.
Once a suitably random private key has been generated, the next step is to produce its corresponding public key.
Public key generation
The private key is the starting point for generating the corresponding public key. In Bitcoin and many cryptocurrencies, this is achieved with elliptic curve cryptography (ECC).
ECC is a method of encryption that uses the properties of a specific type of mathematical curve to secure data.
Think of it like plotting a point on a graph based on a specific formula; the formula being the elliptic curve and your private key being the input.
If that sounds complicated, it’s because it is. And that’s a good thing. The mathematical complexities of the ECC algorithm make it practically impossible to reverse-engineer the private key from the public key.
This one-way process prevents anyone with access to the public key from uncovering the private key and, by extension, accessing the associated digital assets or data.
Wallet address generation
To facilitate crypto transactions, the public key undergoes a transformation to become something more manageable and user-friendly: the wallet address.
This involves hashing. Hashing is a process where data (in this case, the public key) is passed through a specific algorithm to produce a unique, fixed-size string of characters. Bitcoin uses the SHA-256 algorithm, followed by the RIPEMD-160 algorithm.
This two-step hashing condenses the public key into a shorter form while ensuring that the result is unique. The hashed public key is then further processed to create the actual wallet address.
After this, the address is encoded using a method known as Base58Check. This encoding technique is used to convert the binary hash into an alphanumeric string, making it more readable and less prone to errors.
The final product is the wallet address that users interact with. This allows users to send and receive digital currencies without needing to use the public key.
Why cryptography makes Bitcoin more secure
In a decentralized system like Bitcoin, trust and security are not enforced by a central authority but by cryptography. The computational infeasibility of deriving the private key from the public key is what makes Bitcoin resistant to fraud and hacking attempts.
However, the security of a private key depends also on how it is stored. Keys are stored in wallets. If someone else gains access to your wallet, they can access your private key, and hence, control your funds. Therefore, wallet security is essential.
Wallets come in various forms, including:
- Hardware wallets (physical devices)
- Software wallets (programs installed on a computer or smartphone)
- Paper wallets (a physical copy of both public and private keys).
Key storage and management at scale
Businesses deal with large amounts of assets, making the security of private keys a critical concern.
The typical setup suitable for individual users–a single hardware wallet, private key and backup phrase–is impractical at an institutional level. Institutions need to consider aspects like governance, risk management, operational security, and regulatory compliance.
Institutions tend to require custom solutions that feature a range of different custody options, including:
- Highly secure self-custody cold storage wallets for treasury reserves
- Hot or warm wallets with an operational float for day-to-day business
- Exchange wallets for trading
- Muti-sig wallets requiring more than one key to approve transactions.
Key takeaways
In conclusion, here are the essential points to remember:
- Bitcoin is private by design (though not completely anonymous), as the wallet address, used for transactions, is derived from the public key, while the private key remains secret.
- The security strength of Bitcoin lies in the computational difficulty of deriving a private key from its public key, providing a strong defense against unauthorized access.
- For institutions, managing cryptographic keys requires custom solutions that balance strict security measures with operational flexibility.
Fortris handles digital asset treasury operations for enterprise business.
Want to learn more? Book a demo today.
